XAI-Based Microarchitectural Side-Channel Analysis for Website Fingerprinting Attacks and Defenses

Website Fingerprinting attacks aim to track the visited websites in browsers and infer confidential information about users. Several studies showed that recent advancements in Machine Learning (ML) and Deep Learning (DL) algorithms made it possible to implement website fingerprinting attacks even though various defense techniques are present in the network. Nevertheless, trained models for website detection are not analyzed deeply to identify the leakage sources, which are not always visible to both attackers and Cyber Threat Intelligence engineers. This study explains ML and DL models in the context of microarchitecture-based website fingerprinting attacks. In the attack model, performance counters and cache occupancy side channels are implemented on Google Chrome and Tor browsers. After training ML and DL models, LIME and saliency map XAI methods are applied to examine the leakage points in the side-channel data. To match the leakage samples in the measurements to the network traces, a novel dataset is collected by utilizing Google Chrome and Firefox browser developer tools. Next, the efficiency of explainable methods is analyzed with XAI metrics. Finally, an XAI-based obfuscation defense technique is proposed as a countermeasure against microarchitecture-based website fingerprinting attacks. For more information: https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=9556572
FortuneTeller: Predicting Microarchitectural Attacks via Unsupervised Deep Learning
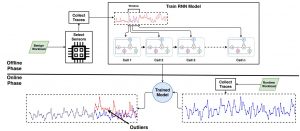
Fortuneteller, for the first time, leverages the superiority of RNNs to learn complex execution patterns and detect unseen microarchitectural attacks in real-world systems. FortuneTeller models benign workload patterns from a microarchitectural standpoint in an unsupervised fashion, and then it predicts how upcoming benign executions are supposed to behave. Potential attacks and malicious behaviors will be detected automatically when there is a discrepancy between the predicted execution pattern and the runtime observation. We implement FortuneTeller based on the available hardware performance counters on Intel processors, and it is trained with 10 million samples obtained from benign applications. For the first time, the latest attacks, such as Meltdown, Spectre, Rowhammer, and Zombieload are detected with one trained model and without observing these attacks during the training. We show that FortuneTeller achieves the best false positive and false negative trade-off compared to existing works under realistic workloads
and target implementations with the highest F-score of 0.9970. For further information: Arxiv